Security at Reltio
Reltio takes the protection of customer data seriously. Reltio customers leverage the Reltio Data Cloud to bring together data from internal, external and third-party sources to create a single customer view. Reltio has implemented security measures to manage customer’s PII, sensitive PII, and PHI data with the applicable level of care.
Reltio Data Cloud is cloud native and leverages security regimes from world leading public cloud providers, Amazon Web Services (AWS), Microsoft Azure (Azure), and Google Cloud Platform (GCP), as well as Reltio’s own internal data security practices, to deliver Reltio services to our customers.

Development and Testing
Reltio develops code to the OWASP Top Ten standard. Reltio engineering staff are trained on the OWASP standard and must re-train on an annual basis. Reltio application software may not be released without quality assurance testing that includes OWASP Top Ten test cases for regression testing as part of a major release. Reltio includes peer review as part of the code development process.
Reltio follows separation of duties as part of the system development life cycle separating developers, quality assurance and release management roles. Developers, support, and quality assurance will not have the ability to update code in a production environment.
Quality assurance processes will align with requirements of 21 CFR Part 11. Reltio maintains change controls, testing validation and other deliverables to support 21 CFR Part 11 documentation requirements.
Reltio Cloud System Access
The security and privacy of your data are our highest priorities at Reltio, and we will continue to uphold the highest standards of data protection and information security to safeguard your tenants and data. Single Sign-On (SSO) is the recommended best practice authentication method for all Reltio customers. The Platform supports Single Sign On (SSO) access for customers with both SAML 2 and OAuth 2 protocols.
Customers choosing not to leverage SSO will have to enable multifactor authentication (MFA) to enhance the security of Reltio accounts which can directly access your data. This significantly reduces the risk of unauthorized access, even if a password is compromised. It also helps comply with various regulatory standards and best practices for data protection.
The Platform provides role-based access controls (RBAC) for customers to maintain access rights to its tenants. Customers are responsible for user, group and role management within customer’s deployment and for administering RBAC access through the Reltio Console or Reltio APIs.
The Platform authenticates all access requiring a SAML assertion or a tenant id, user id, and complex password. Authorization is denied by default and only customers who have explicitly granted access to a Reltio resource may perform functions in the Platform.
Reltio support and administrative access to customer production systems is restricted. Customers must authorize Reltio access in writing. A Reltio manager must approve the access in an internal ticket and the staff member must have a valid business need.
Network System Access
The Platform maintains a virtual private network (VPN) in front of its hosting vendor network. Access to the VPN requires authenticated access with multi factor authentication. In addition, network access is further restricted behind the VPN with bastions. Reltio maintains RBAC controls over user and group access to servers on each subnet. Reltio Information Security maintains control over the access to these resources.
Hypervisor access to the hosting vendor consoles requires multi factor authentication to access resources. Authorization is further restricted by RBAC controls inside the hypervisor. Reltio Information Security maintains control over the access to these resources.
Reltio Information Security restricts access to the customer production network through RBAC controls with the principle of least privilege. A Reltio manager must approve the access in an internal ticket and the staff member must have a valid business need for such access. Information Security has the right to restrict or rescind access.
Data Encryption
The Platform encrypts customer data both at-rest and in-transit. At-rest data is encrypted with AES-256 and in-transit using TLS 1.2 with NIST-approved cipher suites. Customer data may only be accessed via the Platform through proper authentication through the user Interface or through proper authentication through the Reltio API. Administrative tasks can be completed by authorized Reltio staff provided access through role based access control (RBAC) and enforcing the principle of least privilege.
Customers may also register for Reltio Shield which allows customers to generate their own encryption key and to encrypt customer data at the database level. Reltio Shield customers will have control over the encryption key generation and rotation policy via an API.
Data Backups
The Platform creates encrypted backups of customer data on a daily basis.
Logical Data Separation
Reltio does not combine or co-mingle customer data across different data partners or customers. Partners and customers must authenticate against a specific customer tenant. Each tenant has its own database keyspace. Customer data is separated from other customers and such separation aligns with legal discovery requirements.
System Logging
The Platform maintains an activity log of all system activity including login, create, read, update and delete activity. Customer users can see their own activity logs and customer administrators may view activity logs for the entire system via activity log API call. Customers may export this data to a SIEM or other reporting tool via the Reltio API. Activity logs are maintained for a minimum of one year and the Platform will retain logs longer depending on customer requirements.
Reltio maintains system logs for its servers, network, hypervisor, and intrusion detection logs. Logs are maintained for one (1) year. Logging includes common server events including but not limited to logins and failed login attempts, privilege escalation, suspect commands, installation of unapproved applications, external access attempts, etc. Reltio has developed alerts for its SIEM and IDS that Reltio reviews on a regular cadence.
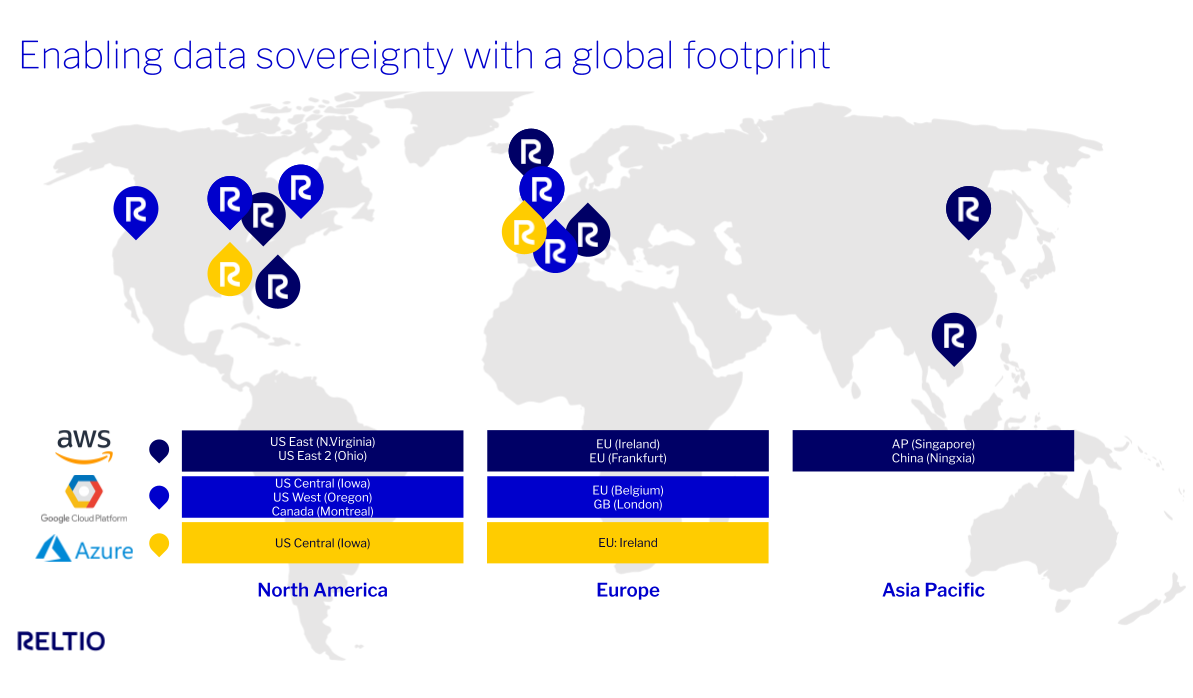
Data Center Locations & Security
Reltio hosts its Platform and associated customer data with AWS, Azure, and GCP. Reltio’s primary cloud platform is located within AWS US East (Virginia) and GCP Central (Iowa) data centers. The Platform distributes its application and database nodes across multiple availability zones enabling application resilience and scalability. Reltio benefits from AWS, Azure, and GCP experience operating and securing physical data centers and securing the hosting vendor cloud.
Reltio Data Cloud infrastructure is hosted in data centers located in the following regions:
AWS North America x2, AWS EU, AWS Ireland, AWS Asia Pac x1, AWS China, Azure North America, GCP North America x2, GCP EUx1, GCP GB (London)
AWS, Azure, and GCP maintain physical security measures designed to provide physical data security and formal physical access procedures.
They adhere to the principle of least privilege. Access is granted for legitimate business needs and limited to the minimum level of access required to complete the task. Access is revoked when staff leave or change positions. They maintain physical controls to safeguard the assets within their respective data center facilities and monitor electrical, mechanical, and life support systems and equipment so that any issues can be immediately identified. AWS, Azure, and GCP conduct preventative maintenance on their respective data centers to maintain the continued operability of data center equipment.
- For more information on AWS physical security see AWS’s website.
- For more information on GCP physical security see GCP’s website.
- For more information on Azure’s physical security see Azure’s website.
Reltio reassess AWS, Azure and GCP annually as part of our third-party vendor security program. Reltio does not have physical servers in our offices.
Business Continuity and Disaster Recovery
Reltio uses ISO 22301 to structure its Business Continuity Plan (BCP) and Disaster Recovery Plan (DR). The BCP and DR include processes required to address a number of different disaster scenarios including application and database outages, natural disasters, fires, pandemics, and data breaches. Contact data and processes are documented, as well as alternate communication mechanisms. Reltio Information Security, in collaboration with other Reltio departments, tests its Business Continuity and Disaster Recovery Plans annually.
In order to build application resilience, Reltio distributes Platform database nodes across a minimum of three AWS, GCP, and Azure zones, as well as having multiple servers within a zone. Data is replicated, load balanced and runs active-active across all zones enabling application and data resilience as well as improved scalability.
For enterprises with highly stringent data availability, resilience, and security needs, Reltio provides the Reltio Business Critical Edition. Please contact the account team for more information.
Security FAQs
Do you have additional security documentation for users available?
You can review our security documentation on docs.reltio.com.
Where will my data be stored?
Please see the list of data centers above. Reltio does not host data at our office or have an on prem solution.
Do you follow OWASP standards?
Yes, Reltio develops code to the OWASP Top Ten Standard & engineers are trained on the OWASP standard.
Do you support single sign-on?
Yes, the Reltio platform supports Single Sign On (SSO) access for customers with both SAML 2 and OAuth 2 protocols.
Do you support multifactor authentication?
Yes. MFA is available for all users, who can enroll in their preferred authenticator apps. Users without MFA will receive Time-Based One-Time Passwords (TOTPs) via email until they enroll in an authenticator app.
Where can I get more information about the Reltio API?
You can review our API documentation on docs.reltio.com.
Do you publish release notes for system users?
Yes, you can see our weekly release notes & major release notes on docs.reltio.com.